Book: Cyber War
Book: Cyber War
So this is on my nightstand
Cyber War by Richard Clark.
http://www.amazon.com/Cyber-War-Threat- ... 0061962244
Mostly the run of the mill doom, except real.
$this->bbcode_second_pass_quote('', 'D')aily Beast, 03.18.15
China Reveals Its Cyberwar Secrets
In an extraordinary official document, Beijing admits it has special units to wage cyberwar—and a lot of them. Is anybody safe?
A high-level Chinese military organization has for the first time formally acknowledged that the country’s military and its intelligence community have specialized units for waging war on computer networks.
China’s hacking exploits, particularly those aimed at stealing trade secrets from U.S. companies, have been well known for years, and a source of constant tension between Washington and Beijing. But Chinese officials have routinely dismissed allegations that they spy on American corporations or have the ability to damage critical infrastructure, such as electrical power grids and gas pipelines, via cyber attacks.
Now it appears that China has dropped the charade. “This is the first time we’ve seen an explicit acknowledgement of the existence of China’s secretive cyber-warfare forces from the Chinese side,” says Joe McReynolds, who researches the country’s network warfare strategy, doctrine, and capabilities at the Center for Intelligence Research and Analysis.
Cyber War by Richard Clark.
http://www.amazon.com/Cyber-War-Threat- ... 0061962244
Mostly the run of the mill doom, except real.
$this->bbcode_second_pass_quote('', 'D')aily Beast, 03.18.15
China Reveals Its Cyberwar Secrets
In an extraordinary official document, Beijing admits it has special units to wage cyberwar—and a lot of them. Is anybody safe?
A high-level Chinese military organization has for the first time formally acknowledged that the country’s military and its intelligence community have specialized units for waging war on computer networks.
China’s hacking exploits, particularly those aimed at stealing trade secrets from U.S. companies, have been well known for years, and a source of constant tension between Washington and Beijing. But Chinese officials have routinely dismissed allegations that they spy on American corporations or have the ability to damage critical infrastructure, such as electrical power grids and gas pipelines, via cyber attacks.
Now it appears that China has dropped the charade. “This is the first time we’ve seen an explicit acknowledgement of the existence of China’s secretive cyber-warfare forces from the Chinese side,” says Joe McReynolds, who researches the country’s network warfare strategy, doctrine, and capabilities at the Center for Intelligence Research and Analysis.
http://www.thedailybeast.com/articles/2 ... crets.html
So, how skeerd should I be?
.
The legitimate object of government, is to do for a community of people, whatever they need to have done, but can not do, at all, or can not, so well do, for themselves -- in their separate, and individual capacities.
-- Abraham Lincoln, Fragment on Government (July 1, 1854)
-- Abraham Lincoln, Fragment on Government (July 1, 1854)
-

Pops - Elite

- Posts: 19746
- Joined: Sat 03 Apr 2004, 04:00:00
- Location: QuikSac for a 6-Pac
Re: Book: Cyber War
That would depend on if we have plans for a color revolution in Hong Kong or Beijing. If we don't; then I wouldn't worry too much about it; it'll likely always be commercial stuff they are after. We're a huge customer; you don't go break your customers ability to buy stuff from you, though you might like to know lots of their nifty secrets before anyone else.
Yes we are, as we are,
And so shall we remain,
Until the end.
And so shall we remain,
Until the end.
- AgentR11
- Light Sweet Crude
- Posts: 6589
- Joined: Tue 22 Mar 2011, 09:15:51
- Location: East Texas
Re: Book: Cyber War
Relax. Drug resistant bacteria or virus will probably get yah. Of course, the Chinese can do almost everything we can do.
Cyber Commander Expects Damaging Critical Infrastructure Attack
$this->bbcode_second_pass_quote('', 'A')dm. Michael Rogers, USN, who leads both the National Security Agency and U.S. Cyber Command, predicts a damaging attack to critical infrastructure networks within the coming years. If an attack happens, the agency and Cyber Command will coordinate a response along with other government agencies and potentially the private sector organizations that own many of the networks.
Critical infrastructure is the backbone of the nation’s economy, security and health, according to the Department of Homeland Security (DHS). It includes the systems and networks, whether physical or virtual, so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, the economy or national public health or safety. It also includes broadband and wireless networks and the massive power and communications grids.
“I fully expect that in my time as commander, someone—whether it’s a nation-state, group or individual—will attempt to engage in destructive activity against one of those, if not more than one,” Adm. Rogers says.
Cyber Commander Expects Damaging Critical Infrastructure Attack
$this->bbcode_second_pass_quote('', 'A')dm. Michael Rogers, USN, who leads both the National Security Agency and U.S. Cyber Command, predicts a damaging attack to critical infrastructure networks within the coming years. If an attack happens, the agency and Cyber Command will coordinate a response along with other government agencies and potentially the private sector organizations that own many of the networks.
Critical infrastructure is the backbone of the nation’s economy, security and health, according to the Department of Homeland Security (DHS). It includes the systems and networks, whether physical or virtual, so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, the economy or national public health or safety. It also includes broadband and wireless networks and the massive power and communications grids.
“I fully expect that in my time as commander, someone—whether it’s a nation-state, group or individual—will attempt to engage in destructive activity against one of those, if not more than one,” Adm. Rogers says.
Targeting SCADA Systems
U.S. Cyber Command Presentation: Assessing Actions Along the Spectrum of Cyberspace Operations
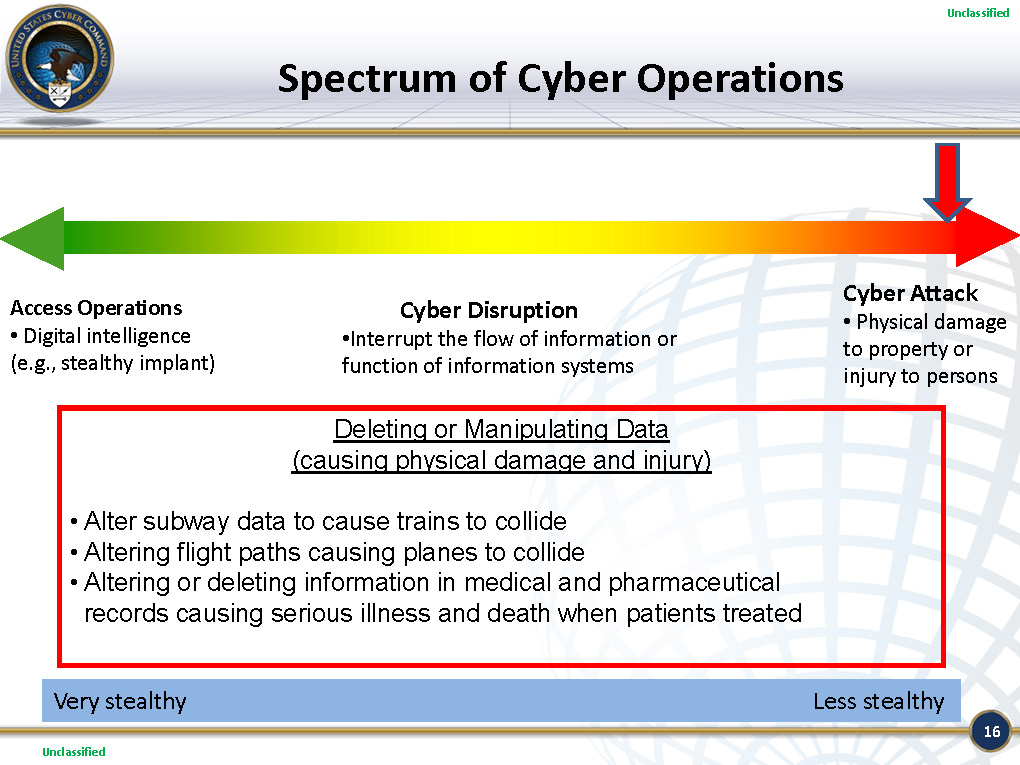
Chinese Capabilities for Computer Network Operations and Cyber Espionage
$this->bbcode_second_pass_quote('', '.').. Chinese capabilities in computer network operations have advanced sufficiently to pose genuine risk to U.S. military operations in the event of a conflict. A defense of Taiwan against mainland aggression is the one contingency in the western Pacific Ocean in which success for the United States hinges upon the speed of its response and the ability of the military to arrive on station with sufficient force to defend Taiwan adequately. PLA analysts consistently identify logistics and C4ISR infrastructure as U.S. strategic centers of gravity suggesting that PLA commanders will almost certainly attempt to target these system with both electronic countermeasures weapons and network attack and exploitation tools, likely in advance of actual combat to delay U.S. entry or degrade capabilities in a conflict.
The effects of preemptive penetrations may not be readily observable or detected until after combat has begun or after Chinese computer network attack (CNA) teams have executed their tools against targeted networks. Even if circumstantial evidence points to China as the culprit, no policy currently exists to easily determine appropriate response options to a large scale attack on U.S. military or civilian networks in which definitive attribution is lacking. Beijing, understanding this, may seek to exploit this gray area in U.S. policymaking and legal frameworks to create delays in U.S. command decision making.
The decision to employ computer network operations and INEW capabilities rests with the senior political and military leadership and would be part of a larger issue of employing force during a crisis. Once that decision was made, however, the operational control for the military use of CNO rests with the PLA’s Third and Fourth Departments of the General Staff Department (GSD). The Third Department (3PLA), China’s primary signals intelligence collector is likely tasked with the network defense and possibly exploitation missions. The Fourth Department (4PLA), the traditional electronic warfare arm of the PLA, likely has the responsibility for conducting network attack missions.
“There are three classes of people: those who see. Those who see when they are shown. Those who do not see.” ― Leonardo da Vinci
Insensible before the wave so soon released by callous fate. Affected most, they understand the least, and understanding, when it comes, invariably arrives too late.
Insensible before the wave so soon released by callous fate. Affected most, they understand the least, and understanding, when it comes, invariably arrives too late.
-

vox_mundi - Intermediate Crude
- Posts: 3939
- Joined: Wed 27 Sep 2006, 03:00:00
Re: Book: Cyber War
I really hate the term "cyber-war". When the Five Eyes do it, it's "bulk collection" or "targeted operations", when the Chinese do it it's "cyber-war".
It's hacking/surveillance etc. Not war. And the NSA "Equation Group" has been operating for at least 14 years and are the most capable in the world, so if we're going to be using the term, who are the cyber-warmongers?
It's hacking/surveillance etc. Not war. And the NSA "Equation Group" has been operating for at least 14 years and are the most capable in the world, so if we're going to be using the term, who are the cyber-warmongers?
What we think, we become.
-

davep - Senior Moderator
- Posts: 4579
- Joined: Wed 21 Jun 2006, 03:00:00
- Location: Europe
Re: Book: Cyber War
$this->bbcode_second_pass_quote('davep', 'I') really hate the term "cyber-war". When the Five Eyes do it, it's "bulk collection" or "targeted operations", when the Chinese do it it's "cyber-war".
It's hacking/surveillance etc. Not war.
It's hacking/surveillance etc. Not war.
I'm not talking about stealing the secret formula for DaisyMae Feminine Deodorant Spray or my porn password or a hack on the PO.com homepage, that's just part of modern life — anything electronic should be seen as virtually publin knowledge IMHO.
I'm talking about an actual destructive attack on infrastructure.
The legitimate object of government, is to do for a community of people, whatever they need to have done, but can not do, at all, or can not, so well do, for themselves -- in their separate, and individual capacities.
-- Abraham Lincoln, Fragment on Government (July 1, 1854)
-- Abraham Lincoln, Fragment on Government (July 1, 1854)
-

Pops - Elite

- Posts: 19746
- Joined: Sat 03 Apr 2004, 04:00:00
- Location: QuikSac for a 6-Pac